
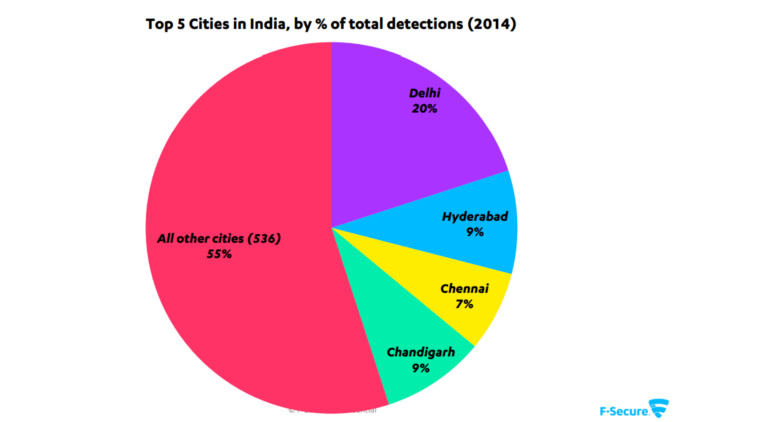
F-Secure Labs in its “The State of Internet in India” report has labelled New Delhi as the most infected city in 2014 out of 540 cities it reviewed. Around 20 per cent of malicious activities were detected from New Delhi. Other most infected cities include Hyderabad (9 per cent), Chennai (7 per cent) and Chandigarh (9 per cent). “This means that the chances of getting infected in these cities are higher,” said Su Gim Goh, security advisor, F-Secure.
According to the report, the top malware infection in Indian cyber space continues to be Botnet related.
Through Botnets, hackers aim to take control of PCs and use them for spamming, DDoS or other malicious activities to make money. The report also said that banking related malware has been consistently topping the charts in India. “Cyber criminals find India to be a very profitable location mainly due to lack of awareness and ease of infecting users. Indians are comfortable with pirated softwares and are mostly reluctant to update applications regularly,” said Goh.
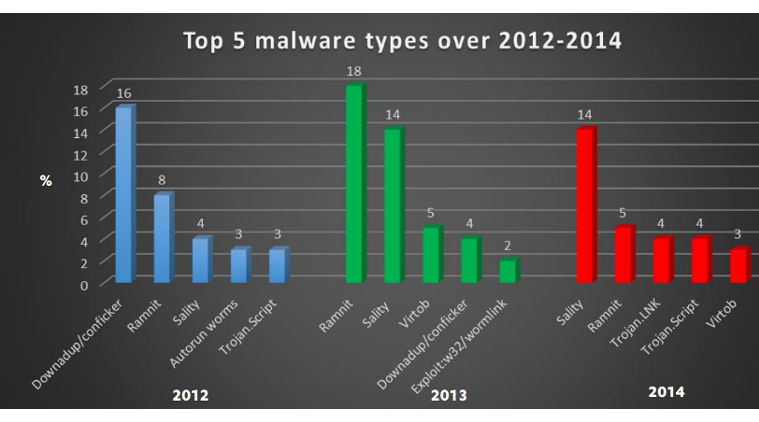
In 2014, the top five malware types in India were Sality (14 per cent), Ramnit (5 per cent), Trojan.LNK (4 per cent), Trojan.Script and Virtob (3 per cent).
Over 2013-2014, the report observed a decline in Autorun worms, Downadup/conficker and Exploit:w32/wormlink. Downadup or conficker infects older Windows operating systems. The decline is due to the fact that PCs in India are moving away from Windows XP.
Banking malwares like Sality and Ramnit continue to dominate over the last two years. The Ramnit malware steals bank usernames and passwords and mostly spreads through USB drives.
“On the mobile threat landscape, premium rate SMS is still the major reason behind a high number of SMS-related malware in the Android platform in India. This is in line with what the CERT-In (Computer Emergency Response Team of India) found in December of 2014,” F-Secure said.
F-Secure Labs also detected the maximum number malicious activities on Android smartphones happening from Mumbai (22 per cent) followed by New Delhi, Chennai, Gurgaon, Hyderabad, Bangalore, Pune and Kolkata.
The most common types of Android malwares are Android/SMSSend and Android/FakeInst. “Once infected with any of these, it sends text messages (with a link to itself or a different threat) to a specific number. These SMMes are typically send to numbers on the contact list and these are also capable of sending SMSes to premium rate numbers,” Computer Emergency Response Team of India (CERT-In) said in its latest advisory to Android smartphone users in the country.
Another Android smartphone malware is Android/SMSreg. The application collects information like API key, Application ID, carrier name, device manufacturer, device model, GPS location, IMEI number, network operator, package name and SDK version. “People get attempted to use free WiFi services and do not realise the amount of personal information they might end up sharing just to browse the Internet for free,” said Goh.








