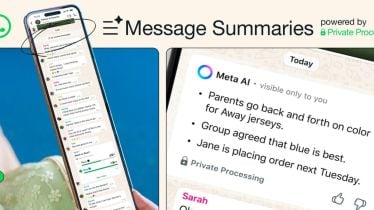
WhatsApp has rolled out a new AI-powered new feature powered by Meta AI called Message Summaries aimed at making it easier for users to stay on top of messages they haven’t yet read. This functionality leverages Meta AI to create brief overviews of conversations, allowing users to stay updated on missed messages in both individual and group chats without having to sift through long threads of text.
The Message Summaries tool is powered by Meta’s Private Processing technology, enabling Meta AI to create conversation overviews. According to WhatsApp, this system is designed to protect your privacy, ensuring that no external party — including Meta or WhatsApp — can access your messages or the generated summaries. Additionally, other participants in the chat won’t be able to view your message summaries.
Describing the latest feature, WhatsApp in a blogpost stated, “a new option that uses Meta AI to privately and quickly summarise unread messages in a chat, so you can get an idea of what is happening, before reading the details in your unread messages.”
How the feature works:
Meta, the company behind WhatsApp, describes Private Processing as a specialized computing framework layered on a Trusted Execution Environment (TEE).
This security-focused setup enables users to interact with the AI assistant within a secure cloud-based environment. It follows a specific threat model and is built around three core principles.
The first principle, secure data handling, ensures that no internal or external system can access user information while it’s being processed or during transmission to the infrastructure.
The second is enforceable protections—if someone tries to tamper with the secure processing mechanism, the system either halts all operations or exposes the alteration through a system of provable transparency.
That transparency mechanism is the third key component, making sure any attempt to breach or alter the secure framework can be traced and verified.